PWN! PWN! PANG! Part2
Introduction
After covering the basics (which don’t seem very basic), let’s talk about tools today
Since we are studying PWN under Linux, please perform the following operations under Linux
What if you only have Windows?
- Option 1: Use VMware Workstation Pro to install a Linux virtual machine (This is what I did)
Small Tip: Some Linux distributions (like Kali) can be downloaded as ready-made virtual machine files from their official websites. If you haven’t installed a VM before
(or are too lazy to), this method is worth trying
- Option 2: Use WSL2 (Well, WSL2 is small in size and now comes with a GUI, but it’s not very comfortable to use compared with VMs)
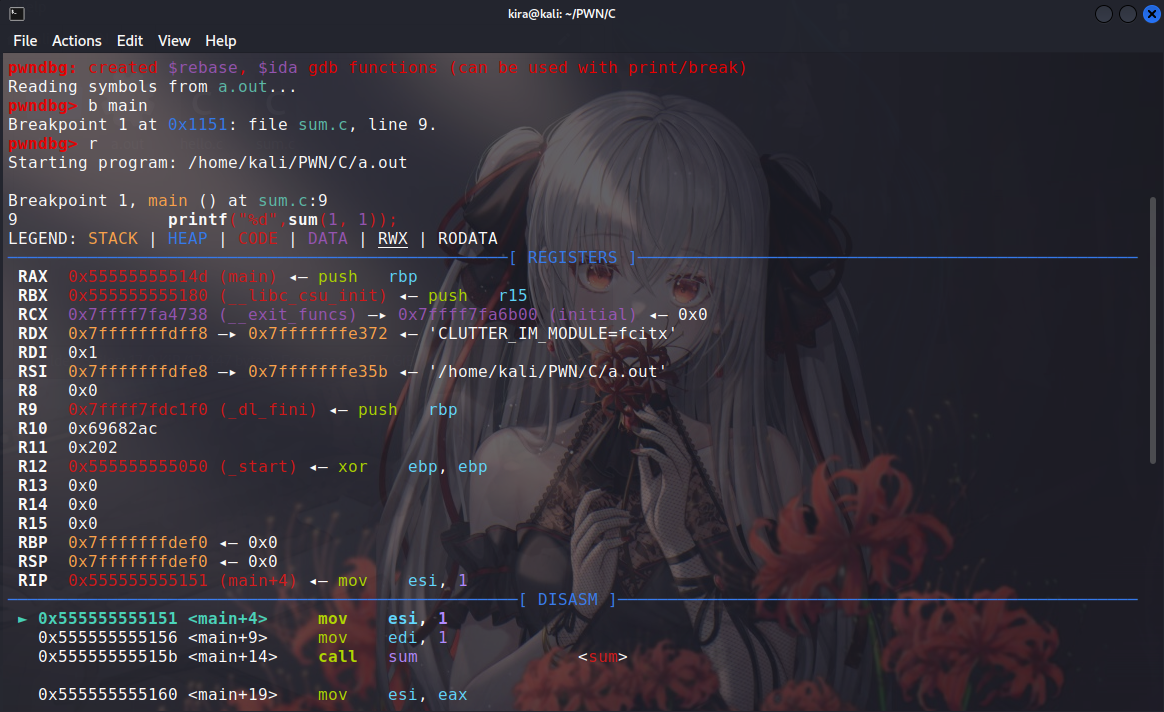
PWNDBG
pwndbg is a plugin for Linux GDB specifically designed for PWN, which helps us debug programs
Installation
Most Linux systems come with gdb pre-installed, but let’s just go over the installation process
Debian-based systems
sudo apt install gdb
yum-based systems Just switch to Debian ;)
sudo yum -y install centos-release-scl
sudo yum-config-manager --enable rhel-server-rhscl-7-rpms
sudo yum -y install devtoolset-7
scl enable devtoolset-7 bash
After installing gdb, we can install pwndbg
git clone https://github.com/pwndbg/pwndbg.git
cd pwndbg
./setup.sh
Some Tips Related to Installation
Note: Please do not delete or arbitrarily move the pwndbg directory, as it may cause pwndbg to not start properly
If pwndbg does not start properly after installation or a system update, please check the path
sudo vi ~/.gdbinit
After executing the command, you should see a line
source other_content/pwndbg/gdbinit.py
Make sure to change the content after source to the path of gdbinit.py in your pwndbg folder
Tip: If you wish to stop using pwndbg, simply remove this line
Usage
Most of the usage is similar to gdb. Here are a few frequently used commands
b function_name # set a breakpoint at a function
b *address # set a breakpoint at an address
r # run
n # execute the next instruction or skip a function
s # step into a function
q # quit gdb
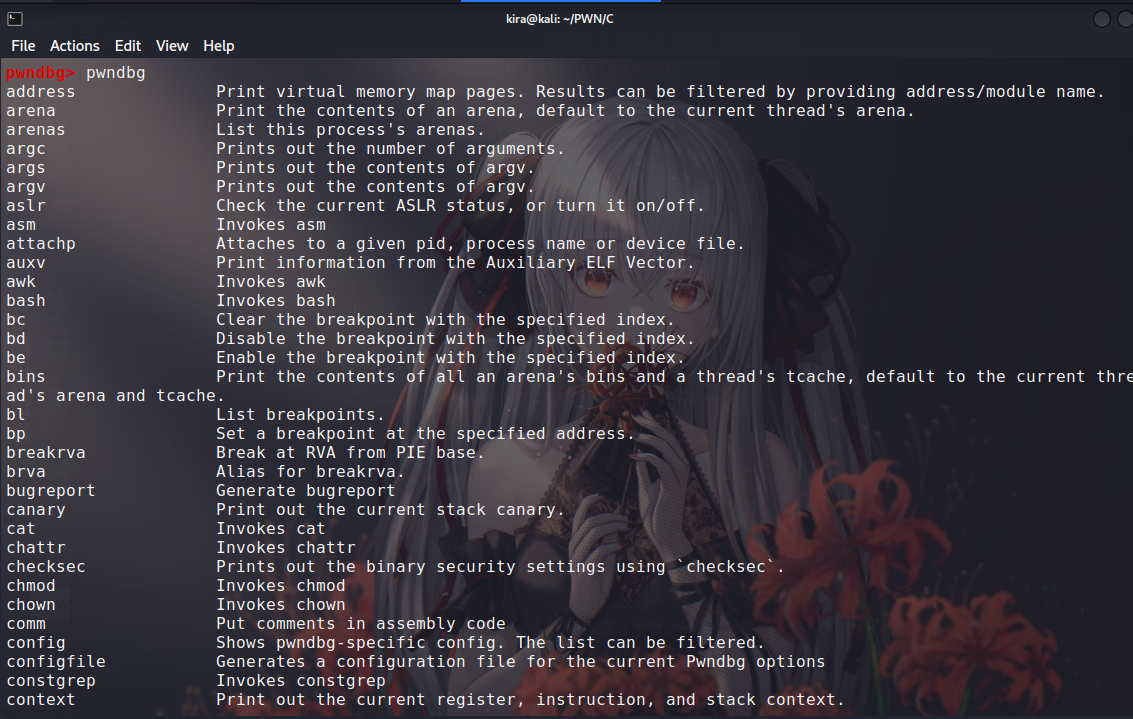
As for the special features of pwndbg, they can be viewed using the pwndbg command
PWNTOOLS
This is a third-party Python library for pwn
Installation
You can install pwntools simply using
pip install pwntools
Don’t have pip? Hurry up and install Python 3!!! (Most Linux systems should have it pre-installed = = )
Usage
Use it just like any standard Python library
from pwn import *
Let me mention a few commonly used commands, qaq (others will be discussed as needed). Of course, it’s best to check the documentation
io = process("./program_name") # Similar to "listening" to a local program with PWNTools, then use the 'io' variable for data transmission
io.send("content") # send data (no automatic newline at the end)
io.sendline("content") # send a line of data (automatically adds a newline at the end)
io.recv()
io.recvline() # receive data, similar to the above two functions
# Note: In the PWN process, it's crucial to choose the above four commands based on the target program's input/output functions, as these subtle differences could prevent you from getting a shell
io.interactive() # switch to interactive mode, where we can "enjoy the acquired Shell
PWN?PWN! Let’s Get Hands-On Experiences
Task: Familiarize yourself with the use of pwntools
Let’s run and see what this little program is all about ;)
PS: If the terminal indicates insufficient permissions, please give the program executable permissions
chmod +x tools
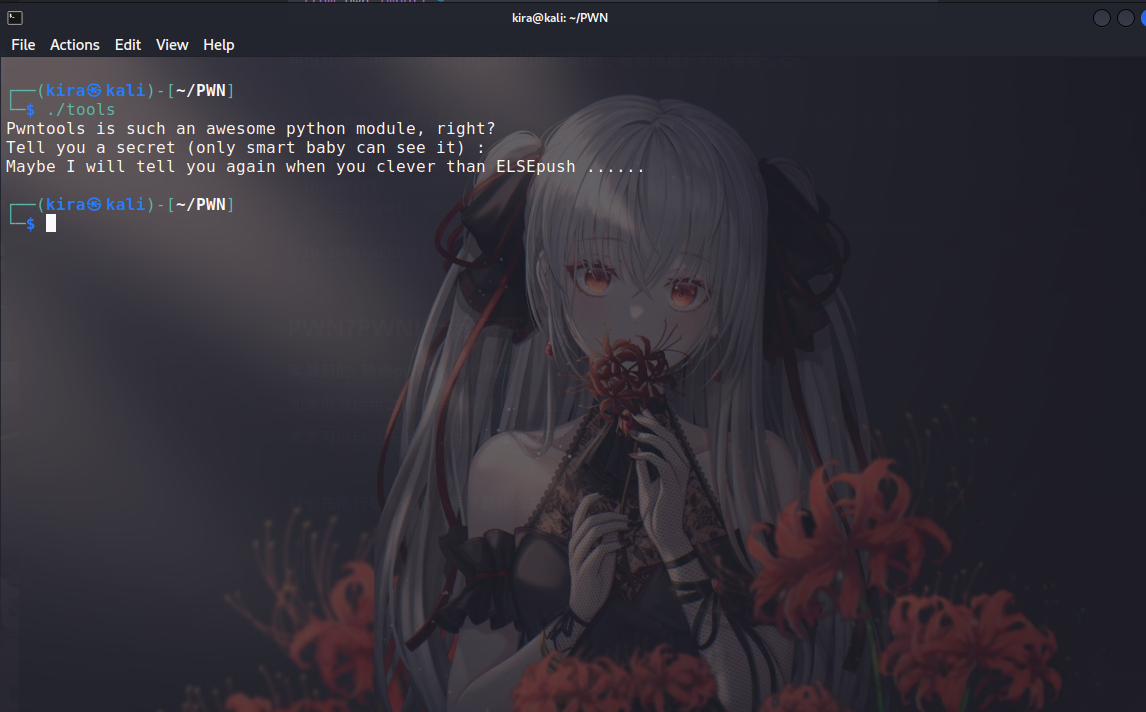
Output
Pwntools is such an awesome python module, right?
Tell you a secret (only smart baby can see it) :
Maybe I will tell you again when you clever than ELSEpush ......
The program says: Pwntools is a great python module and wants to tell us a secret that only smart people can see
So how can we see this so-called secret? Running it directly won’t show it ()
Based on what we learned and the program’s output, we can deduce that we should use pwntools to view it
$ python3
Python 3.9.9 (main, Jan 12 2022, 16:10:51)
[GCC 11.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from pwn import *
>>>
Since the program has no input, only output, we have to use recv() or recvline() functions, qaq
EXP:
from pwn import *
io = process("./tools")
io.recvline()
io.recvline()
io.recvline()
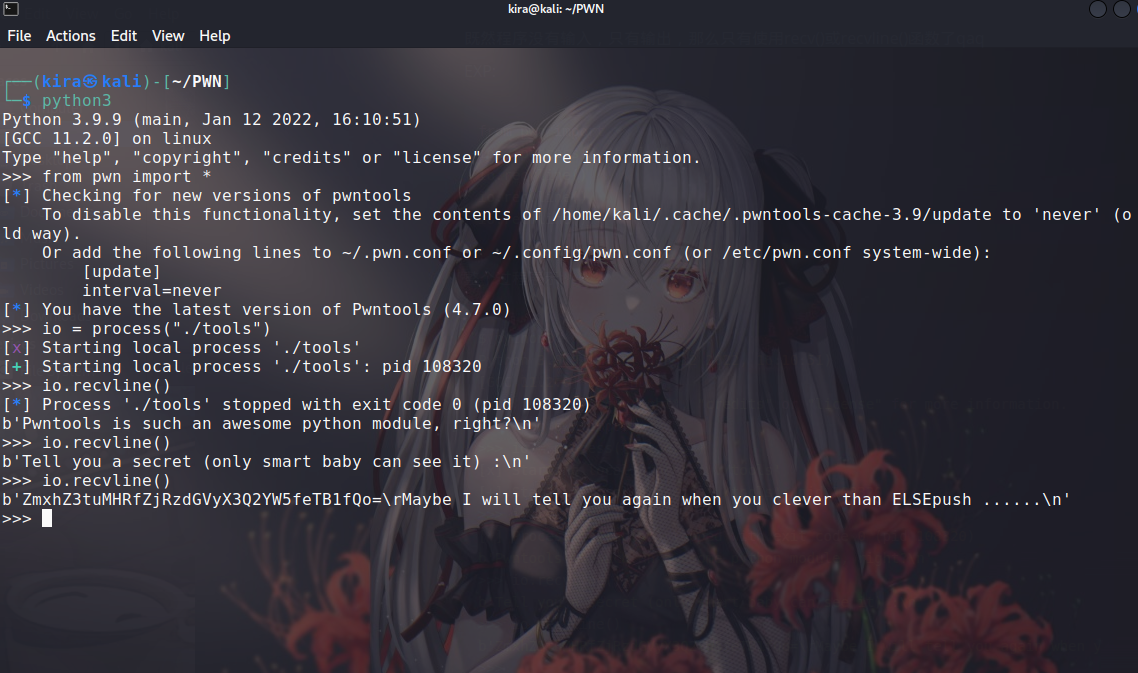
The whole process:
$ python3
Python 3.9.9 (main, Jan 12 2022, 16:10:51)
[GCC 11.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from pwn import *
>>> io = process("./tools")
[x] Starting local process './tools'
[+] Starting local process './tools': pid 108320
>>> io.recvline()
[*] Process './tools' stopped with exit code 0 (pid 108320)
b'Pwntools is such an awesome python module, right?n'
>>> io.recvline()
b'Tell you a secret (only smart baby can see it) :n'
>>> io.recvline()
b'ZmxhZ3tuMHRfZjRzdGVyX3Q2YW5feTB1fQo=rMaybe I will tell you again when you clever than ELSEpush ......n'
>>>
The END= =
To Be Continued…
Part of the translations by GPT-4
